Preparation
- An android device, in this case, Sony xperia Z is used
- Root permission required
- Linux Deploy for deploy image via chroot/proot
- OpenVPN
Step
1. Root android device for superuser permission
2. Install Linux Deploy from play store or custom apk.
- Install Linux Deploy
3. Install linux
- Click download icon to select which image to deploy
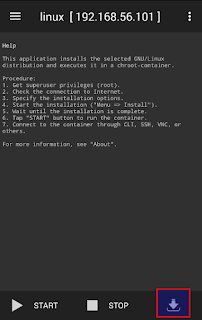
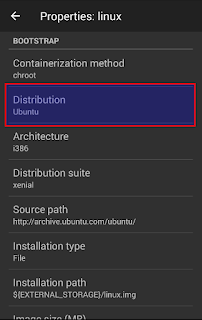
- Select which distribution and suite to use
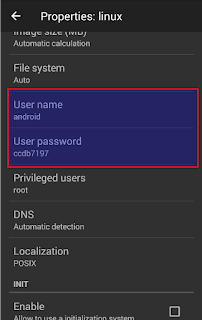
- Set user name & password
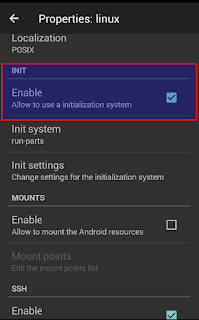
- Allow init system
- Enable SSH server
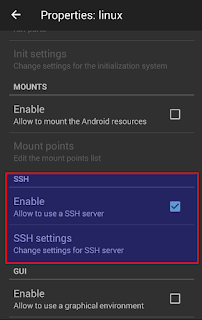
- Deploy distribution
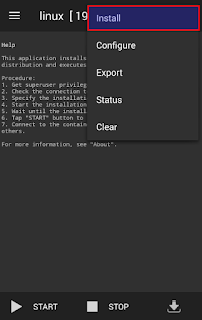
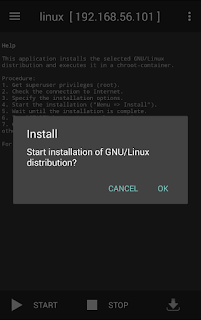
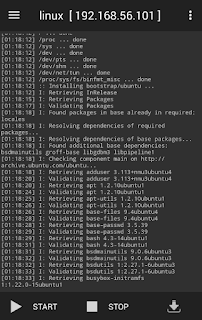
- After installation completed, start linux
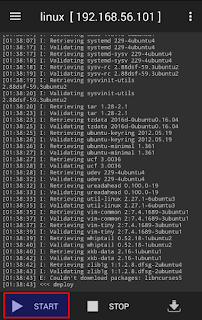
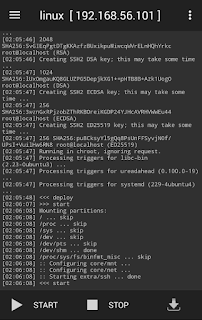
4. Connect to android via SSH
5. Install OpenVPN
- Install required packages
- Create certification folder and edit vars configuration
- Edit vars as blow
- Build ca, server and client certification
- Copy required certification to the path of openvpn
- Clone configuration file from sample config
- Edit server.conf
- Edit server.conf as blow, modify what your need
- Modify networking config sysctl.conf
- Modify content to allow transfer traffic from vpn
- Make changes work
- Edit firewall rules
- Add following content to allow route from vpn subnet to wireless
- Edit firewall configuration
- Allow forward policy
- Add firewall rule for vpn and ssh
- Make changes work. (In this case, there was some error but I ignore that)
- Start openvpn
- Validate result





